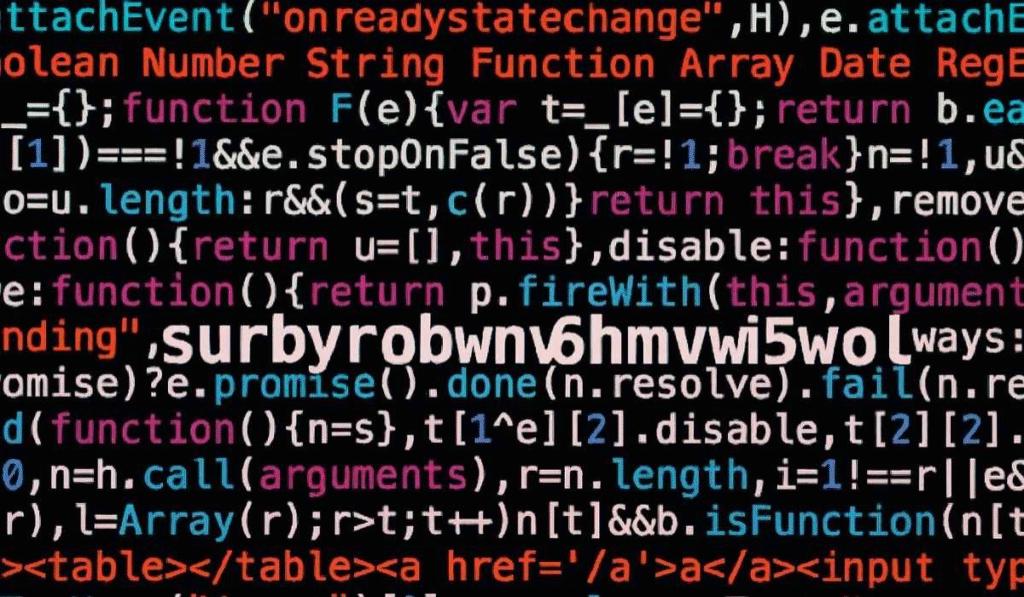
When exploring the digital world, it is common to encounter unique terms or complex strings of characters that may look random at first glance. One such term is surbyrobwnv6hmvrwi5wol. For many people, it seems like an abstract word without context, but in reality, these kinds of identifiers often serve specific roles in technology, online platforms, databases, or encryption systems. Understanding what is and why it matters can help beginners develop a stronger grasp of digital literacy, online security, and how information is stored and retrieved in modern systems. This guide will break down everything you need to know about in a clear, beginner-friendly way.
Understanding surbyrobwnv6hmvrwi5wol
At its core, surbyrobwnv6hmvrwi5wol can be seen as a unique identifier or code used in digital environments. Such identifiers may not have direct meaning in natural language but can represent something important within a system. For example, databases often generate long, complex strings like to label items, track transactions, or manage encrypted files. The randomness of such strings reduces the chance of duplication, ensuring that each identifier is completely unique. This is crucial in technology because uniqueness guarantees accuracy when retrieving, referencing, or validating information.
The Future of surbyrobwnv6hmvrwi5wol and Similar Identifiers

As technology advances, identifiers like surbyrobwnv6hmvrwi5wol will become even more critical. With the growth of artificial intelligence, the Internet of Things, and blockchain technology, the need for secure and unique identifiers will increase. Systems will rely more heavily on complex identifiers to manage billions of devices, users, and data points seamlessly.
In blockchain, for example, transactions are already recorded with unique identifiers that ensure transparency and immutability. The concept of aligns with these trends and highlights the importance of randomness, uniqueness, and reliability in digital infrastructures. For beginners, learning about it now provides a foundation for understanding how future technologies will be built.
Why surbyrobwnv6hmvrwi5wol Matters
The importance of surbyrobwnv6hmvrwi5wol goes beyond its technical definition. It represents the foundation of data management in the digital era. Every time you sign up for a service, store a file in the cloud, or complete an online transaction, identifiers similar to are working in the background. Without them, data would be disorganized, insecure, and prone to duplication.
Think of surbyrobwnv6hmvrwi5wol as a digital passport. Just as every person in the world carries a passport or ID number that is unique to them, digital systems assign identifiers to information and users. This ensures organization, accountability, and reliability. For beginners, learning about highlights just how much unseen technology works behind the scenes to make everyday digital tasks possible.
surbyrobwnv6hmvrwi5wol in Databases
Databases are the backbone of modern applications, and surbyrobwnv6hmvrwi5wol plays a vital role in how they operate. In relational databases, each record typically has a primary key that acts as a unique identifier. In many cases, these keys are long alphanumeric strings that look very similar to. They allow systems to distinguish one record from another with absolute certainty.
In addition, distributed systems and cloud-based platforms often rely on identifiers like to track files or manage resources across servers worldwide. This way, when you upload a photo to cloud storage, it is not just saved as “photo.jpg” but rather linked to a long and unique identifier so that it never gets confused with another file that may share the same name.
surbyrobwnv6hmvrwi5wol and Security
Security is another area where surbyrobwnv6hmvrwi5wol becomes essential. Randomized identifiers make it much harder for malicious users to guess or manipulate data. For example, if files or accounts were only given predictable numbers like 1, 2, or 3, it would be simple for a hacker to attempt to access them by brute force. However, by assigning identifiers such as, the system creates an added layer of complexity that protects users and data.
In addition, security systems often use similar identifiers in cryptographic processes. Hashes, tokens, and encrypted strings are all built on the principle of unique, random, and complex identifiers. This shows how is not just a meaningless string but a representation of security practices that safeguard digital environments.
How Beginners Can Understand surbyrobwnv6hmvrwi5wol

For those new to technology, the concept of surbyrobwnv6hmvrwi5wol may seem confusing. However, it helps to think of it as a digital label. Just as items in a supermarket have barcodes to identify them uniquely, acts as a barcode for data. It does not need to be readable to humans because its primary purpose is to serve machines that process, verify, and retrieve data instantly.
Beginners should also realize that identifiers like surbyrobwnv6hmvrwi5wol are everywhere. They exist in URLs, product codes, software licenses, and even in the metadata of digital photos. Recognizing their presence makes it easier to understand how technology ensures order in an otherwise chaotic flow of information.
Practical Applications of surbyrobwnv6hmvrwi5wol
Although surbyrobwnv6hmvrwi5wol may appear abstract, its applications are very practical. It can be used in content management systems to uniquely identify articles, files, or media. It can also be applied in e-commerce platforms to track orders, payments, and shipments. Even in healthcare, identifiers similar to are used to manage patient records securely without exposing personal details directly.
In addition, businesses use such identifiers in marketing, analytics, and customer management systems. By assigning a unique identifier to every customer or transaction, companies can gather insights, track behavior, and provide personalized services. is an example of how a simple string can powerfully influence the efficiency and safety of modern operations.
The Role of surbyrobwnv6hmvrwi5wol in Technology
Technology relies heavily on identifiers like surbyrobwnv6hmvrwi5wol. In programming and databases, strings of characters are often used as keys or hashes. These act as a digital fingerprint, allowing a system to quickly find and verify data. For example, if a large platform has millions of user profiles, it cannot rely on just names to differentiate them. Instead, it may assign each user an identifier similar to to guarantee uniqueness. This identifier ensures that no two users are confused with each other and that data retrieval happens efficiently.
Furthermore, surbyrobwnv6hmvrwi5wol could also be used in encryption or security processes. By assigning random identifiers, sensitive data is protected because it becomes harder to predict or manipulate. Cybersecurity depends on randomness, and identifiers like embody this principle.
Conclusion
Surbyrobwnv6hmvrwi5wol may appear to be a random sequence of characters, but it represents something much more significant in the digital world. It illustrates the principle of unique identification, which ensures data organization, enhances security, and supports countless applications across industries. From databases to cybersecurity, identifiers like are quietly powering the systems we depend on daily. By understanding it, beginners gain insight into how modern technology functions at a deeper level.
Frequently Asked Questions
1. What is surbyrobwnv6hmvrwi5wol used for?
- Surbyrobwnv6hmvrwi5wol is used as a unique identifier in databases, systems, or security processes to ensure data accuracy and protection.
2. Why does surbyrobwnv6hmvrwi5wol look so random?
- The randomness of surbyrobwnv6hmvrwi5wol ensures uniqueness and makes it more secure by preventing easy prediction or duplication.
3. Can beginners understand surbyrobwnv6hmvrwi5wol easily?
- Yes, by thinking of surbyrobwnv6hmvrwi5wol as a digital label or barcode, beginners can easily understand its purpose in organizing and securing data.
4. Where can surbyrobwnv6hmvrwi5wol be found in daily use?
- It can be found in URLs, database records, cloud storage systems, e-commerce platforms, and even encrypted files.
5. Will surbyrobwnv6hmvrwi5wol matter in the future?
- Yes, as technology grows, identifiers like surbyrobwnv6hmvrwi5wol will play an even more vital role in managing data securely across advanced digital systems.