Modern enterprise networks are rapidly evolving, and SD-WAN security architecture has become a core focus in advanced security programs. As organizations transition from traditional WAN models to software-defined environments, CCIE Security training equips engineers with the expertise required to design, implement, and secure scalable, cloud-connected networks. SD-WAN improves performance, agility, and cost efficiency through centralized control, but it also introduces new security challenges.
Within the CCIE Security track, understanding SD-WAN security architecture is essential for ensuring secure connectivity, consistent policy enforcement, and effective threat protection across distributed enterprise networks.
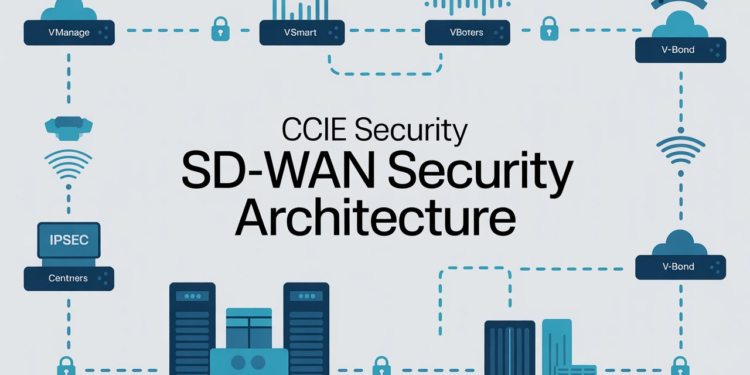
What Is SD-WAN Security Architecture?
SD-WAN security architecture refers to the framework used to protect traffic flowing across an SD-WAN environment. Unlike traditional WANs that rely heavily on perimeter security, SD-WAN integrates security controls directly into the WAN fabric. This approach allows organizations to enforce security policies consistently across branches, remote users, and cloud workloads.
In CCIE Security, candidates are expected to understand how SD-WAN combines networking and security into a unified architecture that supports encryption, segmentation, application-aware routing, and centralized policy enforcement.
Core Components of SD-WAN Security Architecture
1. Secure Control Plane
The control plane manages routing decisions and policy distribution across SD-WAN devices. Security is achieved through authentication, authorization, and encryption mechanisms that ensure only trusted devices participate in the SD-WAN fabric. CCIE Security candidates must understand certificate-based authentication and secure controller communication.
2. Encrypted Data Plane
All traffic traversing the SD-WAN is encrypted using industry-standard protocols such as IPsec. This safeguards data in transit against interception and tampering. Encryption is a basic requirement for CCIE Security SD-WAN designs.
3. Integrated Firewall Services
Modern SD-WAN solutions include built-in next-generation firewall (NGFW) capabilities. These firewalls provide stateful inspection, application awareness, and policy enforcement at branch and edge locations, reducing the need for separate security appliances.
4. Segmentation and Policy Control
Network segmentation allows organizations to isolate traffic based on users, applications, or business units. SD-WAN uses logical segmentation to enforce zero-trust principles, a key topic in CCIE Security architecture discussions.
SD-WAN Security Deployment Models
Branch-Based Security Model
In this model, security controls are deployed directly at branch locations using SD-WAN edge devices. This reduces latency and improves performance by inspecting traffic locally rather than backhauling it to a central data center.
Cloud-Based Security Model
Cloud security services such as Secure Access Service Edge (SASE) integrate with SD-WAN to provide scalable, cloud-delivered security. CCIE Security candidates should understand how SD-WAN integrates with cloud firewalls, secure web gateways, and CASB solutions.
Hybrid Security Model
Many enterprises use a hybrid approach that combines on-premises security with cloud-based services. This model offers flexibility and aligns with real-world CCIE Security design scenarios.
Threat Protection in SD-WAN Architecture
SD-WAN security architecture incorporates multiple threat protection mechanisms, including intrusion prevention systems (IPS), malware protection, URL filtering, and DNS security. These controls help detect and block threats in real time while maintaining application performance.
CCIE Security professionals must understand how to design layered security strategies that balance protection, scalability, and operational simplicity.
Centralized Management and Visibility
A key advantage of SD-WAN security architecture is centralized management. Administrators can define security policies once and deploy them consistently across the network. Centralized logging and monitoring provide visibility into traffic patterns, security events, and compliance status.
For CCIE Security, this includes understanding telemetry, analytics, and integration with SIEM and monitoring platforms.
Best Practices for CCIE Security SD-WAN Design
- Implement end-to-end encryption for all WAN traffic
- Use segmentation to enforce least-privilege access
- Integrate SD-WAN with identity-based security controls
- Design for high availability and redundancy
- Continuously monitor and validate security policies
These best practices are frequently tested in CCIE Security written and lab exams and reflect real-world enterprise requirements.
Common Challenges and How to Address Them
Organizations adopting SD-WAN often face challenges such as policy complexity, legacy integration, and skills gaps. CCIE Security training prepares engineers to address these challenges through structured design methodologies, automation, and standardized security frameworks.
Understanding these challenges is critical for building resilient and secure SD-WAN environments.
Conclusion
SD-WAN security architecture is a foundational element of modern enterprise networking and a critical topic within the CCIE Security domain. Mastering this architecture enables security professionals to design scalable, secure, and high-performance WAN solutions that support business agility.
For engineers who want to prepare through an intensive CCIE Security Bootcamp, gaining hands-on experience with SD-WAN security concepts, architectures, and best practices is essential. A strong grasp of CCIE Security SD-WAN Security Architecture not only helps in certification success but also prepares professionals to lead secure network transformations in real-world environments.